‘CyberGuy’: Spring Backup
Protecting your digital life with a reliable physical backup isn’t just a precaution, it’s a necessity. Kurt Knutsson provides the essential checklist for backing up your data.
Chances are you are much closer to suffering an online security disaster than you think. Information about you is widely spread online and losing control of this digital identity can be incredibly embarrassing at best and financially devastating or personally dangerous at worst.
While it may seem overwhelming at first, we are here to help you stay safe online. We have created a list of all the steps to stay safe online. Since there is a lot of information, we suggest you go through it at your own pace.
RECEIVE SECURITY ALERTS, EXPERT TIPS: SUBSCRIBE TO KURT’S NEWSLETTER – THE CYBERGUY REPORT HERE
Woman stressed by online disaster (Kurt “CyberGuy” Knutsson)
Step 1 – Enable automatic updates
Maintaining your software until date It’s one of the easiest ways to stay safe online. Whether you use a Windows machine, a Mac, an iPhone, or an Android smartphone, all of these devices are routinely updated with new security fixes. It’s a good idea to check and make sure your device’s automatic updates are turned on. Here’s how:
Windows 10 Automatic Updates
From the start menu, go to Settings > Update & security > Windows UpdateIn the Windows Update section, you’ll see a variety of options for updating Windows. Here you can set your “active hours” to ensure that Windows automatically restarts and installs updates outside of your waking or working hours.
Windows 11 Automatic Updates
Windows 11 users will click on the Windows icon and proceed to Settings > Windows Update > Advanced optionsFrom here, you can control when Windows Update will run, similar to the “active hours” control in Windows 10.
Mac OS
Mac users can open System Preferences > Software Update and click the “Advanced” button. While in the “Advanced” section, make sure all the boxes are checked as this will ensure that you receive the latest updates. Timely operating system updates.
iOS
If you want to turn on automatic updates with an iPhone, open Settings > General > Software Update and make sure that Automatic Updates It’s on.
Android
If you have an Android device, open Settings > System > Advanced > System Update and ensure the Upgrade system The setting is enabled in.
AUTO PARTS GIANT EXPOSED: 2.3 CUSTOMERS AT RISK DUE TO MASSIVE DATA LEAK
Step 2 – Use strong passwords
Reusing the same password across multiple websites or apps is one of the most common cybersecurity mistakes. If you use the same password for multiple things, it only takes one service breach to expose your other accounts. password manager It is a simple solution to create strong passwords for multiple accounts.

Illustration of how to protect your device (Kurt “CyberGuy” Knutsson)
THE WORLD’S LARGEST STOLEN PASSWORD DATABASE UPLOADED TO A CRIMINAL FORUM
Step 3: Set up and use two-factor authentication
Two factors authentication It’s a great way to add an extra layer of security to your online accounts. Enabling two-factor authentication makes it harder for hackers to access your account, as it will require a one-time code in addition to your password to log in.
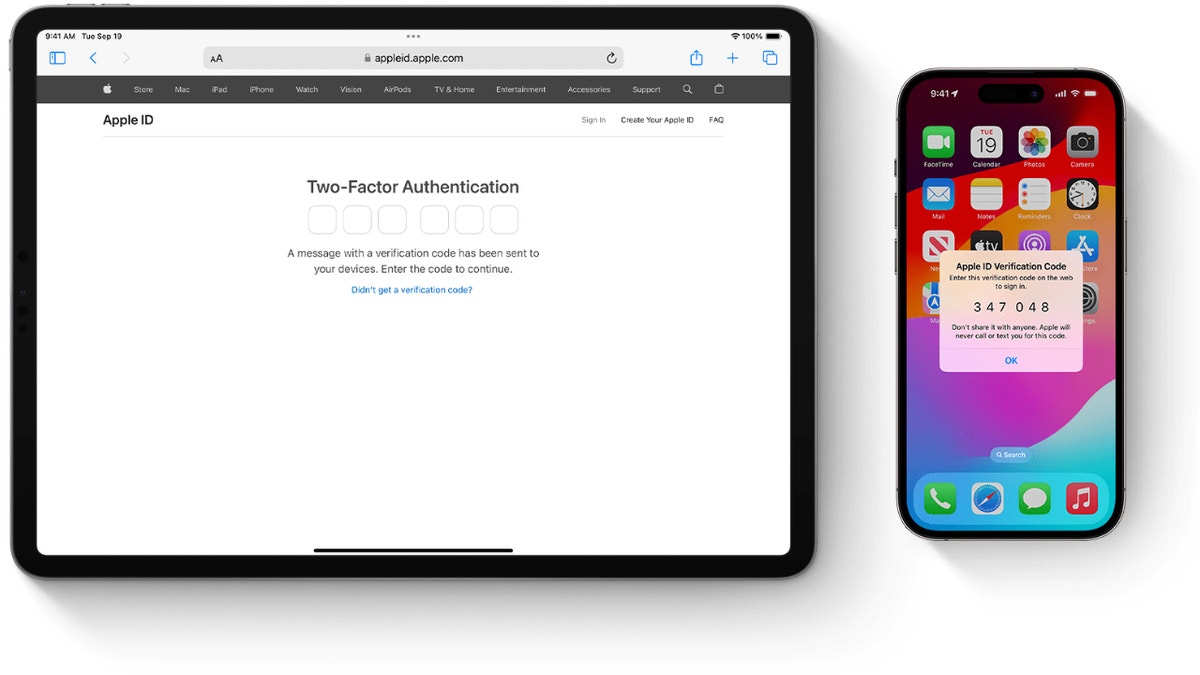
Two-factor authentication displayed on Apple devices (Apple) (Kurt “CyberGuy” Knutsson)
Step 4: Encrypt your computer storage
If you were to lose your laptop, tablet, or phone, all the personal information on those devices could be accessible to whoever finds it. An easy way to protect yourself in this case is to encrypt your devices beforehand. Encryption makes it difficult for hackers to read the data, and while it sounds complicated, the actual process is easy to set up.

Illustration of data on a computer screen (Kurt “CyberGuy” Knutsson)
Step 5 – Locate or erase a lost device
If you’ve lost your device before you can encrypt it, there’s no need to worry too much. It’s easier than ever to locate a lost smartphone or remotely wipe its data. We have an excellent guide on what to do if you’ve lost your device before you can encrypt it. I lost my phone for both Android and iPhone.
You can also use a similar process to locate a lost item. Windows laptop either MacBookAs operating systems have moved to storing information in the cloud, it’s easy to wipe data from a lost laptop. If you lose a laptop in public, we recommend remotely wiping it as soon as possible to ensure a malicious actor doesn’t get a hold of your data.
Step 6 – Have a powerful antivirus software
The best way to protect yourself from clicking on malicious links that install malware that can access your private information is to have antivirus protection installed on all your devices. This can also alert you to any phishing emails or ransomware scams. Get my picks for the best antivirus protection winners of 2024 for your Windows, Mac, Android, and iOS devices.
Step 7: Protect your web browser
We use our web browsers on a daily basis. Whether from a laptop, desktop, or smartphone, you probably use your web browser more than most other applications. Taking a few minutes to regularly update your browser to the latest version, being cautious about the websites you visit, and avoiding suspicious downloads are all critical practices that complement your browser’s security features.
By implementing these security measures, you are protecting your browser, personal information, financial data, and your overall digital identity. Being exposed to a security risk from potential hackers and cybercriminals..
Step 8 – Protect your smartphone
Smartphones now act as extensions of our personal lives and are used for everything from banking to scheduling medical appointments. It’s more important than ever to keep your smartphone secure, and luckily, both Android and iOS have a wide range of built-in features to help protect your personal information.
To improve your iPhone either Android Security: Start by enabling a secure screen lock method, such as a complex passcode, fingerprint recognition, or facial recognition. Be careful when using public wifi networks and consider using a VPN For added security.

A person holding an Android phone (Kurt “CyberGuy” Knutsson)
10 SIMPLE STEPS TO IMPROVE THE SECURITY AND PRIVACY OF YOUR SMARTPHONE
Step 9 – Protect your wireless network
Your home Wi-Fi network can power your smart home devices, but it can also leave you draining power. vulnerable to hackersFortunately, it’s easy to modify your wireless home setup To be extra protected, similar to the steps above, you’ll want to make sure your router has the latest updated firmware and that you’re using two-factor authentication and a strong password for your wireless connection.

People on their computers using a wireless network (Kurt “CyberGuy” Knutsson)
Step 10 – Make regular backups of your data
Regularly backing up your data protects your digital life from hardware failure, theft, or cyberattacks. Choose a reliable backup method that suits your needs, such as cloud storage either External hard drivesSet up automatic backups to run consistently, ensuring all your devices, including smartphones and tablets, are protected. Protect your backups by using strong passwords, enabling two-factor authentication for cloud storage, or encrypting physical backups.
Periodically test your backups by restoring files to ensure that your system is working properly. Remember that a solid backup strategy is an essential component of your overall cybersecurity plan, providing protection and peace of mind.
Step 11 – Invest in personal data removal services
In today’s digital landscape, your personal information can end up in numerous online databases and people search sites without your knowledge or consent. These data aggregators collect and sell your information, potentially exposing you to privacy risks and unwanted requests. Using a data removal service can help mitigate these risks by systematically removing your personal information from these databases.
While no service promises to remove all of your data from the Internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites on an ongoing basis over an extended period of time.
By reducing your digital footprint, you decrease the chances of your personal information being misused for identity theft, targeted advertising, or other privacy-invading practices. While it is difficult to completely erase your online presence, using a data removal service is an effective step toward regaining control over your personal information and improving your overall online privacy and security. Check out my top picks for data removal services here.
Kurt’s key takeaways
Securing your online presence can seem like a daunting task, but remember that it’s all about taking small, consistent steps. Think of it as building a digital fortress—each measure you implement is another brick in your cybersecurity wall. Don’t feel pressured to tackle everything at once. Start with the basics, like enabling automatic updates and using strong passwords, and then gradually work your way up to additional steps. The digital world is constantly evolving, and so should our security practices.
How has your approach to online security changed over the years and what motivated those changes? Let us know by writing to us at Cyberguy.com/Contact.
For more tech tips and security alerts, subscribe to my free CyberGuy Report newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or tell us what stories you’d like us to cover..
Follow Kurt on his social channels:
Answers to CyberGuy’s most frequently asked questions:
Copyright 2024 CyberGuy.com. All rights reserved.









